Institute proxies
[DEPRECATED] INSTITUTE NO LONGER USES PROXY.
Internet connection inside IIT Kharagpur is provided through an HTTP Proxy server. A proxy server acts as an intermediary for requests from clients seeking resources from internet. For addresses that are on the KGP LAN Network, using the proxy server is not required.
The HTTP Proxy is 172.16.2.30:8080 (as of 6th July, 2017).
The proxy server can be bypassed for the address 10.0.0.0/8 . This CIDR address will bypass the proxy for all addresses on the KGP network.
Setup
Windows
In Windows, most GUI programs will internally use Internet Explorer's proxy settings.
The default proxy settings can be updated by navigating to Internet Explorer's options.
Tools > Internet Options > Connections > LAN settings.
There are some programs however which don't use Internet Explorer's proxy settings. A prominent example of that remains the Windows Store in Windows 8 & 10. They can be set using netsh, or network shell, a command-line utility which allows local or remote configuration of network devices such as the interface.
The following are some relevant commands (Run cmd as an adminisrator and type the following) :
1. netsh winhttp show proxy : This command shows the current proxy setting
2. netsh winhttp reset proxy: This command resets the current proxy setting to a direct connection.
3. netsh winhttp import proxy source=ie : This command sets Internet Explorer as the proxy source for netsh, thus both sharing the same proxy.
Note: For some Windows users, the Git Bash accepts the proxy settings as mentioned below for Linux. In the Git Bash command line, input the following proxies:
http_proxy=http://172.16.2.30:8080/ https_proxy=http://172.16.2.30:8080/ ftp_proxy=http://172.16.2.30:8080/
Linux
In *nix based systems, proxy settings are controlled via environment variables which can be updated in a number of ways. A few of these methods are described below:
Automatic Script
If you are on Debian/Ubuntu, use the script provided at the link to set system-wide proxies for mostly used commands instantly.
https://github.com/thealphadollar/set_proxy_kgp
If you are on some other Linux distribution, please create an issue at the same repository.
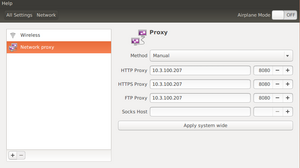
GUI
In most cases, a desktop environment (Unity for example; ships default with Ubuntu) provides a graphical user interface to access network settings under the System Settings > Network option. An option to set up proxies can be found there. You can also use applications like dconf-editor to configure system wide proxy. You can also configure no_proxy settings using this application.
Command Line
Command line interface provides a quick way of updating your environment variables and thus your proxy settings. The proxy values are contained within the following variables - http_proxy, https_proxy, ftp_proxy, socks_proxy, no_proxy. One can update these values using a sample command shown below:
export http_proxy=http://172.16.2.30:8080/
The variable no_proxy contains those addresses for which the proxy access is disabled (useful for certain library websites, Moodle website, DC website etc.,). These settings, however, are not persistent through different login sessions and you must put these commands in your .bashrc (for bash shell) or .zshrc (for zsh shell) to be applied every time on shell startup.
You can also permanently export these settings to root environment settings by editing the /etc/environment file. Open this file with sudo permission using your favorite text editor (vim for example) and paste the following:
http_proxy=http://172.16.2.30:8080/ HTTP_PROXY=http://172.16.2.30:8080/ https_proxy=http://172.16.2.30:8080/ HTTPS_PROXY=http://172.16.2.30:8080/ FTP_PROXY=http://172.16.2.30:8080/ ftp_proxy=http://172.16.2.30:8080/ no_proxy=127.0.0.0/8,::1,10.0.0.0/8
Save and exit. The environment settings should now be always applied to your current environment. Verify this by checking the output of sudo env | grep proxy. It is, however, important to note that some applications might require their own proxy to be set up separately (git, apt-get, wget for example) and you must consult the appropriate man pages. To configure "apt-get" to use proxy add the following lines to "/etc/apt/apt.conf"
Acquire::http::Proxy "http://172.16.2.30:8080"; Acquire::https::Proxy "http://172.16.2.30:8080"; Acquire::ftp::Proxy "http://172.16.2.30:8080";
In case you do not add the proxy options to root's environment, use the -E flag to ask sudo to preserve the existing environment variables. For example: sudo -E add-apt-repository "deb http://us.archive.ubuntu.com/ubuntu/ saucy universe multiverse"
OS X
- Go to System Preferences > Network > Select the appropriate service on the left (eg. WiFi) > Advanced > Proxies, and set both HTTP and HTTPS proxies.
- Proxy bypass rules can be configured at the bottom.
iOS
- Go to Settings > Wi-Fi > Tap on the Wi-Fi network that you've connected to > Scroll down to HTTP Proxy > Set the server and port, and go back to the Wi-Fi screen for the settings to take effect.
- There is no way to configure proxy bypass rules.
Raspberry Pi
1. For apt :
Navigate to the following folder as follows:
cd /etc/apt/apt.conf.d
Create a file called 10proxy:
sudo nano 10proxy
Without authentication add these line:
Acquire::http::Proxy "http://172.16.2.30:8080"; Acquire::https::Proxy "http://172.16.2.30:8080"; Acquire::ftp::Proxy "http://172.16.2.30:8080";
With Authentication add these line :
Acquire::http::Proxy "http://username:[email protected]:8080"; Acquire::https::Proxy "http://username:[email protected]:8080"; Acquire::ftp::Proxy "http://username:[email protected]:8080";
2. For everything else:
Edit this file:
sudo nano /etc/environment
Add these line :
http_proxy=http://172.16.2.30:8080/ HTTP_PROXY=http://172.16.2.30:8080/ https_proxy=https://172.16.2.30:8080/ HTTPS_PROXY=https://172.16.2.30:8080/ FTP_PROXY=http://172.16.2.30:8080/ ftp_proxy=http://172.16.2.30:8080/ no_proxy=127.0.0.0/8,::1,10.0.0.0/8
Android

When connected to any of the mentioned access points, opening WiFi settings and long pressing the current WiFi network will give a Modify Network option. Within this, scroll down and tick the Proxy Server checkbox and enter the IP address and port. This will allow you to use browser, play store and some other applications but WhatsApp and Skype will not work.
However, to use wifi for WhatsApp, Skype, messenger and other applications , you can use applications like Drony, Proxifier, Psiphon, DroidVPN etc. These apps are available in Play Store. Also, it is to be noted that applications like Drony and Proxifier are proxy configuring app, they simply tunnel your whole internet traffic through a proxy server, in our case through IIT Kgp's proxy server whereas Psiphon and DroidVPN are VPN apps. The difference is that in former case , your internet requests are handled by IIT kgp's own server whereas in latter case an outside server handles your internet requests. Using internal server provides you privacy since your actual IP is Also, speed wise Drony and Proxifier are better than Psiphon and DroidVPN. But the advantage of VPN apps over others is that you can access sites blocked by IIT Kgp like Torrents etc.
If the phone can be or is already rooted, applications like ProxyDroid and AutoProxy Lite may provide better experience. However, if you do not prefer to root your phone, use applications like DroidVPN, Psiphon or SurfEasy to configure proxy settings.
Windows Phone
Go to Settings > Wifi and touch on the required connection. It should give an option to setup the proxy.
Bypass
The proxy server does not route connections back inside the local subnet, but silently times out. To connect to a computer inside the KGP network, you need to bypass the proxy for that computer's IP, and make a direct connection. The following is a list of IPs and hostnames for which it is useful to bypass the proxy. An asterisk ( * ) or ( x ) represents any value.
- localhost and 127.0.0.1
- All IPs in KGP's subnet – 10.x.x.x
- *.iitkgp.ernet.in
If you want to configure the no_proxy variable, set it to 10.0.0.0/8,127.0.0.0/8,::1.
For instructions on how to bypass the proxy for your OS or device, see Setup.
Workarounds
KGP's proxies only allow HTTP connections on ports 80 and 443. This means that several much needed tools are broken behind the Great Fire Proxy. Depending on what you are trying to do, the following workarounds might be useful. These instructions are written with *nix based systems in mind, but equivalent alternatives for Windows can be found (often with same name).
Tor
tor anonymises traffic, and has the useful side effect of convincing the proxy that we're making an HTTP connection.
As of September 2015, the institute is actively blocking tor connections, but bridge is not necessary to connect to tor.[1][2]
Browse the Internet through tor
If you only need to access websites through a browser, download the Tor Browser Bundle, which provides a nice and easy to configure GUI setup and is available for Android, Linux, Mac, and Windows.
Setting up tor in Android
- Download Orbot from F-Droid or from Play Store and install.
- Go to Settings > Select Outbound Proxy Type and enter HTTPS. Select Outbound Proxy Host and enter 172.16.2.30 Select Outbound Proxy Port and enter 8080.
- Select 'Select Apps' option and tick those apps along with browsers whose traffic you want to route through tor.
- Go back to main screen and press Start. Swipe from right to left to see connection log. When connected, click on browse and choose a browser.
- To stop tor press Stop and swipe from left to right and turn off 'Apps VPN Mode'
- (Optionally) download Orfox which is a tor browser for android and also if you want to surf onion websites.
Run tor as a daemon
- Set up tor to run as a daemon on some port (eg. 9050). You can usually do this by installing tor using your distro's package manager (eg.
apt-get install tor). - In tor's config file (eg. /etc/tor/torrc), add
HTTPSProxy <KGP proxy host>:<KGP proxy port>. - To make sure everything works, clear any existing HTTP or HTTPS proxy settings, and set your SOCKS proxy to use tor (eg. 127.0.0.1:9050). Go to https://check.torproject.org/, it should say that you're using tor.
Using tor to make the git protocol and OpenShift applications work (on Linux)
- Download the Tor Browser Bundle
- Navigate to the folder ~/.ssh and edit the config file. (You can create one if you don't have it already)
$ cd ~/.ssh $ vim config
Add the following lines to the file to make the git protocol work: [3]
Host github.com
User git
ProxyCommand connect -4 -S localhost:9050 $(tor-resolve %h localhost:9050) %p
- Now, run the following command after unzipping the downloaded archive of Tor:
$ ./start-tor-browser.desktop
- Now, the git protocol should have started working.
To check this, you can run:
git clone [email protected]:metakgp/metakgp.git
Note that for this to work properly, your SSH public key must be added to your GitHub account.
If it is not added [visit this guide on GitHub https://help.github.com/articles/generating-ssh-keys/]
This method can be used to get SSH access to OpenShift RedHat cloud applications as well, by appending to the config file:
Host appname-domain.rhcloud.com
User rhcloud.com
ProxyCommand nc -x localhost:9150 %h %p
Replace appname and domain in the above lines with the appropriate names from the OpenShift dashboard.
Typically, an app that can be accessed at mentorship-gradescrapers.rhcloud.com has:
URL: mentorship-gradescrapers.rhcloud.com appname: mentorship domain: gradescrapers
proxychains
proxychains does TCP and DNS tunnelling through an HTTP server.
- Set up tor as outlined above.
- In proxychains's config file (eg. ~/.proxychains/proxychains.conf), configure tor as a socks proxy (eg.
socks5 127.0.0.1 9050).
Now, programs that make TCP connections on any port should work when run with proxychains. For example, proxychains git clone git://example.com.
ProxyCap is a proxychains alternative for Windows and Mac.
ssh
- Option 1 (recommended): corkscrew tunnels ssh through an HTTP proxy. You need root access on the destination server for this to work.
- Install corkscrew and in ~/.ssh/config, add the following line:
ProxyCommand <path to corkscrew> <proxy host> <proxy port> %h %p. - On the destination server, configure sshd to listen on port 443.
- Pass in the
-p 443option when runningssh.
- Install corkscrew and in ~/.ssh/config, add the following line:
- Option 2: You can use proxychains + tor as outlined above. This will be slower, since the connection is routed through tor. However, it has the advantage of not needing to change the port sshd is listening on.
ssh-socks
If you have a remote machine that can listen on port 443 (as outline above), you can run a local socks proxy server on your machine to tunnel traffic through your remote machine. For example, ssh -D 1080 -p 443 myserver.example.com will start an SSH tunnel on port 1080, now you can use 127.0.0.1:1080 as a SOCKS proxy.
Online ssh clients
Online ssh clients are available to connect to remote server. An advantage of using this is that you do not need any extra softwares/configuration on your local computer or the server. Names of some of the websites are as follows :
Serfish - A free AJAX SSH Client to quickly connect to remote server. (Registration not required)
Shiftedit - An online Web-based IDE with remote connection support. (Registration required)
Banned websites
- Option 1: Use tor as outlined above.
- Option 2 (probably faster speeds): Set up a ssh-socks proxy.
git
- Option 1 (recommended): Check if there's an HTTPS version of the repo URL available, and use that if possible.
- Option 2: Use proxychains and tor as outlined above.
- Option 3: Use corkscrew for cloning, pushing, pulling using SSH instead of HTTPS (This avoids the requirement of having to enter username and password each time.)
Host github.com Hostname ssh.github.com Port 443 ProxyCommand corkscrew 172.16.2.30 8080 %h %p
- Option 4: Override ssh settings to force use of port 443 instead of 22 for github.com. Ref: [1]
Host github.com
Hostname ssh.github.com
Port 443
User git
heroku
- Option 1 (recommended): Running commands on the command line of your heroku instance is not possible. Say you want to apply new migrations on a Ruby on Rails app, then, instead of running:
heroku run rake db:migrate
you can run:
heroku run:detached rake db:migrate
This will run the command (rake db:migrate, in this particular case) on the remote machine, and give another command which can be used to view the logs. The output of this command is similar to:
Running `rake db:migrate` detached... up, run.8799 Use `heroku logs -p run.8799 -a app-name` to view the output.
- Option 2: Use proxychains and tor as outlined above.
UDP
HTTP Tunneling is a way of encapsulating UDP packets in HTTPS protocol. Currently the tor network does not support UDP. However, you can use VPNs to tunnel UDP traffic.
- Install OpenVPN. For windows, there is a convenient GUI app.
- Go to OpenVPN settings and set HTTP proxy 172.16.2.30:8080.
- Get .conf file for an openvpn server. vpngate.net has some free servers, be careful to download TCP conf., and only for servers open on port 443. Paid VPNs with stable connections are also available if you look for them.
- Run OpenVPN GUI as administrator (windows) and add KGP proxy. Load the .conf file you downloaded. This should create a new TUN/TAP device, and internet should now work without a proxy.
The connection will be flaky if using vpngate servers. Don't expect to be able to play online games this way, since tunneling would delay your UDP packets too much to get a good ping, even with stable VPN servers.
sshuttle
sshuttle is more easy and powerful over normal ssh socks tunneling for many reasons :-
- App don't need to use a socks proxy
- Client don't need to have root access on remote machine
- You don't want to create an ssh port forward for every single host/port on the remote network.
It's very simple to use. sshuttle requires corkscrew for tunneling. Steps :-
$ git clone https://github.com/apenwarr/sshuttle- Configure
corkscrewinside~/.ssh/config. A line in the file should be something likeProxyCommand corkscrew 172.16.2.30 8080 %h 443 - Start sshuttle by navigating inside the cloned directory and running
./sshuttle --dns -r username@sshserver 0.0.0.0/0 -vv - Remove all the proxy settings whatsoever from browser, applications, `/etc/environment`, etc. i.e. use Direct Connection.
sshuttle catches every tcp connection and routes it through the ssh server.
nvm
nvm (node version manager) is used to download, compile and install node.
To set proxy for nvm, use the following commands:
export http_proxy=172.16.2.30:8080export https_proxy=172.16.2.30:8080export NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist
npm
npm is a package manager for the JavaScript programming language. It is the default package manager for the JavaScript runtime environment Node.js
To set proxy for npm :-
npm config set proxy http://172.16.2.30:8080npm config set https-proxy http://172.16.2.30:8080
Cloud Computing Services
Several cloud computing services and VPS providers are now available for circumvention. Digital Ocean, Amazon EC2, Vultr, Google Compute Engine are some of the popular providers.
Streisand is a convenient one-click solution to create an IPSec secured personal VPN based on the default L2TP/IP protocol. This protocol is supported by default on Android, iOS, Windows, Linux and several other operating systems.
Digital Ocean is a cloud computing service, which provides SSH access to droplets in their data centers. Digital Ocean doesn't have a free plan, but credit of $50 can be obtained by signing up for the GitHub Student Developer Pack. (All currently enrolled students of the institute are eligible.) Further, Digital Ocean requires a Credit Card to be added as payment method (Credit/Debit card is only take as a payment method. You will not be charged anything on setting up the account, provided you are using student pack), or a $5 remittance through PayPal to get the account started.
Once the account can create droplets, droplets may be used for things such as SOCKS proxies, torrenting content through Command Line torrent clients (such as torrent), or as an OpenVPN server.
History
Before the load balancer proxy was introduced, several proxies could be configured. These proxies had different speeds and availabilities at different times. Some of the older proxies were:
- 144.16.192.247
- 144.16.192.245
- 144.16.192.217
- 144.16.192.218
- 10.3.100.209
- 10.3.100.210
- 10.3.100.211
- 10.3.100.212
In 2014, students were instructed to use a single load balancer proxy.[4] The other proxies no longer work.
Public IPs
The outside world sees one of the following IPs as your IP when you make any network request. This public IP is converted to an internal IP (which is what you see as your machine's IP) by the proxy server using NAT. You may need to whitelist these IPs if setting up an external web service that is frequently accessed from campus.
- 203.110.246.22 (as of 11 August 2015)
- 203.110.246.23 (as of 2 September 2015)
- 203.110.243.23 (as of 12 August 2015)
- 203.110.242.20 (as of 7 September 2017)
- 203.110.242.7 (as of 25 April 2018)
You can see your current public IP at http://www.whatsmyip.org/.
It is important to know this because any activity done by you gets logged with these IPs and corresponds to the name of the institution. For example, if you make an anonymous edit to Wikipedia, it will be logged under these public IPs, and hence any disruptive behavior by single person might lead to an IP ban and unavailability of resources for everyone inside the campus. It's advisable to create an account for such activities wherever possible, or use one of the workarounds suggested in initial sections.
